Key Insights
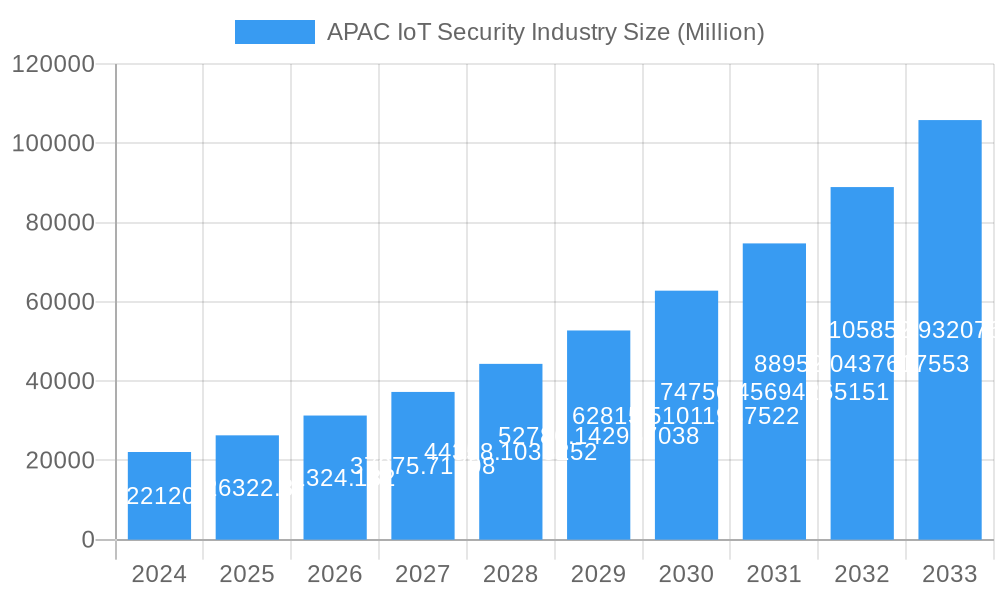
The APAC IoT Security market is poised for explosive growth, driven by the escalating adoption of Internet of Things (IoT) devices across various sectors and the increasing sophistication of cyber threats. In 2024, the market size is estimated at $22.12 billion, with a robust 19% CAGR projected over the forecast period. This expansion is fueled by critical drivers such as the burgeoning demand for enhanced cybersecurity solutions to protect sensitive data generated by interconnected devices in smart homes, wearables, and industrial applications. Furthermore, government initiatives promoting digital transformation and the imperative for regulatory compliance are significantly accelerating market penetration. The rising awareness among businesses and consumers regarding the vulnerabilities inherent in IoT ecosystems necessitates proactive security measures, creating a substantial market opportunity for advanced security solutions.
APAC IoT Security Industry Market Size (In Billion)
The market is segmented into distinct areas, with Network Security and Endpoint Security emerging as dominant segments due to the foundational need to protect the infrastructure and devices themselves. Solutions like Identity and Access Management (IAM) and Intrusion Prevention Systems (IPS) are witnessing high adoption rates as organizations strive for comprehensive threat detection and prevention. Applications in Manufacturing Process Management and Patient Information Management are particularly driving demand in the APAC region, reflecting the critical nature of data security in these industries. Geographically, China is expected to lead the market, followed by India and Japan, owing to their extensive industrialization, rapid technological advancements, and significant investments in IoT infrastructure. However, restrains such as the high cost of implementation and a shortage of skilled cybersecurity professionals in certain areas may pose challenges to the pace of growth, although the overwhelming benefits of robust IoT security are expected to outweigh these concerns.
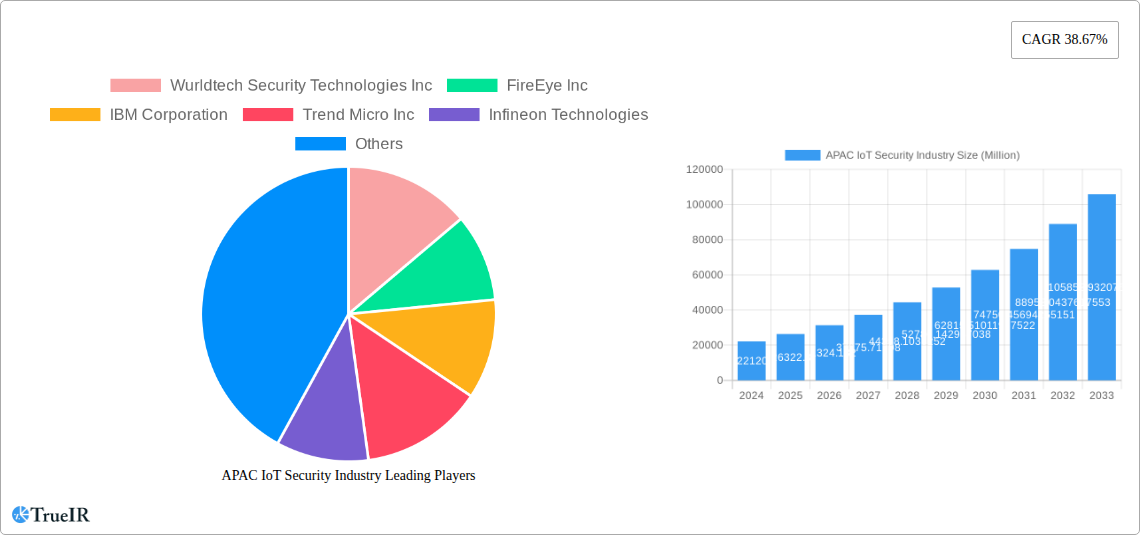
APAC IoT Security Industry Company Market Share
APAC IoT Security Industry Market Structure & Competitive Landscape
The APAC IoT Security industry is characterized by a dynamic and evolving market structure, driven by rapid technological adoption and increasing cybersecurity threats. Market concentration varies across different segments, with some mature areas exhibiting higher consolidation while emerging sectors remain more fragmented. Innovation drivers are paramount, fueled by the relentless pursuit of advanced solutions to secure the burgeoning Internet of Things ecosystem. Regulatory impacts are significant, with governments across the APAC region implementing stricter data protection and cybersecurity mandates, compelling companies to prioritize robust IoT security measures. Product substitutes are emerging, although dedicated IoT security solutions offer superior efficacy against specialized threats. End-user segmentation reveals a diverse demand landscape, from consumer-focused applications like home automation to mission-critical industrial deployments. Mergers & Acquisitions (M&A) trends are on the rise as larger players seek to acquire innovative technologies and expand their market reach, indicating a strategic consolidation phase. The estimated market value is projected to reach xx billion by 2033. The number of M&A deals is expected to be around xx by the end of 2033.
- Market Concentration: Moderate to high in established segments, with key players dominating specific niches.
- Innovation Drivers: Artificial Intelligence (AI), Machine Learning (ML) for threat detection, Zero Trust Architecture, and secure-by-design principles.
- Regulatory Impacts: Growing influence of data privacy laws (e.g., PDPA in Singapore, APPI in Japan) and national cybersecurity frameworks.
- Product Substitutes: General cybersecurity tools that are not specifically tailored for IoT environments.
- End-User Segmentation: Diversified across industrial, commercial, and consumer sectors.
- M&A Trends: Active, with strategic acquisitions aimed at enhancing product portfolios and market share.
APAC IoT Security Industry Market Trends & Opportunities
The APAC IoT Security market is poised for substantial growth, driven by an exponential increase in connected devices and the escalating sophistication of cyber threats. The market size, estimated to be xx billion in the base year 2025, is projected to witness a Compound Annual Growth Rate (CAGR) of xx% during the forecast period of 2025–2033, reaching an estimated xx billion by 2033. This robust expansion is fueled by several key trends. Technological shifts are continuously reshaping the landscape, with a growing emphasis on AI and ML-powered anomaly detection, blockchain for secure device authentication, and edge computing security solutions to process data closer to the source, minimizing latency and improving real-time threat response. Consumer preferences are increasingly leaning towards secure and privacy-preserving IoT devices, pushing manufacturers to integrate security from the design stage. Businesses across various verticals are recognizing the critical need to protect their IoT deployments from data breaches, operational disruptions, and intellectual property theft, leading to a surge in demand for comprehensive security solutions. Competitive dynamics are intensifying, with established cybersecurity giants and specialized IoT security startups vying for market share. Opportunities abound in areas such as industrial IoT (IIoT) security for smart manufacturing, healthcare IoT security for remote patient monitoring, and smart city infrastructure protection. The increasing adoption of 5G technology further amplifies the potential for IoT growth, creating a larger attack surface that necessitates advanced security measures. The proactive approach to cybersecurity being adopted by organizations in China, India, and Japan is a significant trend, highlighting their commitment to securing their digital transformation journeys. Market penetration rates for advanced IoT security solutions are expected to reach xx% by 2033. The adoption of secure device management platforms is projected to grow by xx% annually.
Dominant Markets & Segments in APAC IoT Security Industry
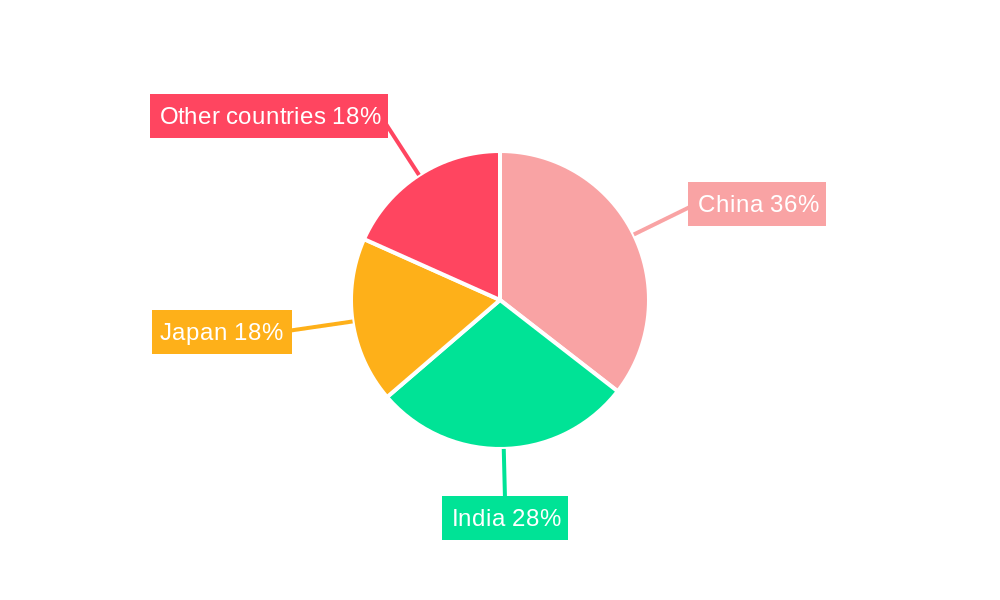
The APAC IoT Security industry exhibits distinct dominance across various segments. Geographically, China, with its massive manufacturing base and rapid technological adoption, is a leading market, followed closely by India and Japan, both investing heavily in digital transformation and smart infrastructure. In terms of the Type of Security, Network Security remains a cornerstone, safeguarding the interconnectedness of IoT devices, but Cloud Security is rapidly gaining prominence as more IoT data and applications migrate to cloud platforms. For Solutions, Identity and Access Management (IAM) is critical for ensuring that only authorized devices and users can access IoT networks and data. Intrusion Prevention Systems (IPS) and Security & Vulnerability Management (SVM) are also key areas of focus. Within Applications, Manufacturing Process Management and Supply Chain Operation security are paramount for industrial IoT deployments, while Home Automation and Wearables represent significant growth areas in the consumer segment. The End-User Verticals seeing the most significant investment in IoT security are Manufacturing, Utilities, and Healthcare, driven by the high stakes of operational continuity and patient data integrity. BFSI is also a major player due to the sensitive nature of financial data. Key growth drivers include robust government initiatives promoting smart city development, the increasing adoption of Industry 4.0 technologies, and rising consumer awareness regarding data privacy and security. The expansion of 5G infrastructure across the region provides a critical foundation for the widespread deployment of IoT devices, further necessitating advanced security solutions.
- Leading Geography: China, followed by India and Japan.
- Key Security Types: Network Security, Cloud Security, Endpoint Security.
- Dominant Solutions: Identity Access Management (IAM), Security & Vulnerability Management (SVM), Intrusion Prevention System (IPS).
- High-Growth Applications: Manufacturing Process Management, Supply Chain Operation, Home Automation, Wearables.
- Primary End-User Verticals: Manufacturing, Utilities, Healthcare, BFSI.
- Growth Drivers: Government smart city initiatives, Industry 4.0 adoption, 5G infrastructure expansion, consumer awareness.
APAC IoT Security Industry Product Analysis
The APAC IoT Security industry is witnessing a wave of innovative products designed to address the unique challenges of securing a diverse range of connected devices. These products focus on providing end-to-end security, from device authentication and data encryption to network monitoring and threat detection. Key advancements include AI-powered anomaly detection systems that can identify unusual device behavior, secure boot mechanisms to prevent tampering, and lightweight cryptographic algorithms suitable for resource-constrained IoT devices. Applications are expanding across smart homes, industrial automation, connected vehicles, and remote healthcare, with tailored solutions emerging for each sector. Competitive advantages are being gained by companies offering integrated security platforms, continuous monitoring capabilities, and seamless integration with existing IT infrastructures. The market is shifting towards proactive security measures, emphasizing secure-by-design principles and the development of solutions that can adapt to evolving threat landscapes. The estimated market value for IoT security products in APAC is xx billion by 2033.
Key Drivers, Barriers & Challenges in APAC IoT Security Industry
Key Drivers: The APAC IoT Security industry is propelled by several powerful drivers. Technological advancements, including the pervasive rollout of 5G networks and the increasing sophistication of AI and ML for threat intelligence, are creating a fertile ground for advanced security solutions. Economic factors such as the massive investments in digital transformation initiatives across industries and the growing recognition of the economic cost of cyber breaches are driving demand. Policy-driven factors, including government mandates for cybersecurity in critical infrastructure and the implementation of data privacy regulations, are creating a compulsory need for robust security frameworks.
Barriers & Challenges: Despite the growth, significant barriers and challenges exist. Supply chain complexities, particularly the reliance on global manufacturing and the difficulty in securing every component of an IoT device, present a substantial risk. Regulatory hurdles, including fragmented and evolving cybersecurity laws across different APAC nations, create compliance complexities. Competitive pressures from both established cybersecurity vendors and new entrants, often vying on price and feature sets, can impact profitability. The sheer scale and diversity of IoT devices, coupled with the limited security expertise within many organizations, also pose considerable challenges to widespread effective implementation of security measures. The estimated cost of IoT security breaches in the APAC region is projected to reach xx billion by 2030.
Growth Drivers in the APAC IoT Security Industry Market
The growth drivers in the APAC IoT Security Industry Market are multifaceted. Technologically, the proliferation of 5G and advancements in AI for threat detection are foundational. Economically, significant investments in smart manufacturing, smart cities, and digital healthcare are fueling demand for secure IoT infrastructure. Regulatory tailwinds, such as government mandates for critical infrastructure protection and emerging data privacy laws across countries like Singapore, Japan, and South Korea, are compelling organizations to prioritize IoT security. Furthermore, increasing consumer awareness regarding data security and privacy is pressuring device manufacturers to embed robust security features. The growing adoption of Industry 4.0 principles globally is also a major catalyst.
Challenges Impacting APAC IoT Security Industry Growth
Several challenges are impacting the growth of the APAC IoT Security Industry. Regulatory complexities, with varying cybersecurity standards and data localization requirements across different APAC nations, create a fragmented compliance landscape. Supply chain issues, including the vulnerability of hardware components to tampering and the difficulty in ensuring end-to-end security throughout the manufacturing process, remain a significant concern. Competitive pressures are intense, with a crowded market often leading to price wars and difficulties in differentiation. Moreover, the sheer volume and diversity of IoT devices, coupled with a shortage of skilled cybersecurity professionals, present ongoing challenges for effective deployment and management of IoT security solutions. The estimated cost of a single IoT security breach is xx million.
Key Players Shaping the APAC IoT Security Industry Market
- Wurldtech Security Technologies Inc
- FireEye Inc
- IBM Corporation
- Trend Micro Inc
- Infineon Technologies
- Gemalto NV
- Symantec Corporation (NortonLifeLock Inc)
- ARM Holdings PLC
- Sophos Group PLC
- Intel Corporation
Significant APAC IoT Security Industry Industry Milestones
- August 2022: Truvisor announced its partnership with One Identity, a unified identity security provider. The partnership would allow Truvisor to deliver One Identity solutions through their resellers' channels in Singapore, the Philippines, and Indonesia. This collaboration aims to enhance identity and access management for IoT deployments in Southeast Asia.
- April 2022: Swimlane, a low-code security automation provider, announced the launch of Swimlane Cloud in the Asia-Pacific Japan (APJ) region. Swimlane's interactive dashboards and automated, easily customizable workflows reduce the mean time to respond and ultimately help organizations ensure continuous compliance and prevent breaches, significantly impacting incident response capabilities for IoT security threats.
Future Outlook for APAC IoT Security Industry Market
The future outlook for the APAC IoT Security Industry market is exceptionally promising, driven by continued digital transformation and the ever-increasing interconnectedness of devices. Growth catalysts include the ongoing expansion of 5G networks, which will enable more sophisticated and data-intensive IoT applications, thereby necessitating advanced security measures. Strategic opportunities lie in the development of AI-driven, predictive security solutions that can proactively identify and neutralize threats before they impact operations. The increasing focus on edge computing security and decentralized security architectures will also open new market avenues. Furthermore, the growing demand for industry-specific IoT security solutions, particularly in sectors like healthcare and manufacturing, presents substantial market potential. The projected market value of xx billion by 2033 underscores the immense growth trajectory ahead.
APAC IoT Security Industry Segmentation
-
1. Type of Security
- 1.1. Network Security
- 1.2. Endpoint Security
- 1.3. Application Security
- 1.4. Cloud Security
- 1.5. Other types of security
-
2. Solutions
- 2.1. Identity Access Management (IAM)
- 2.2. Intrusion Prevention System (IPS)
- 2.3. Data Loss Protection (DLP)
- 2.4. Unified Threat Management (UTM)
- 2.5. Security & Vulnerability Management (SVM)
- 2.6. Network Security Forensics (NSF)
- 2.7. Other solutions
-
3. Applications
- 3.1. Home Automation
- 3.2. Wearables
- 3.3. Manufacturing Process Management
- 3.4. Patient Information Management
- 3.5. Supply Chain Operation
- 3.6. Customer Information Security
- 3.7. Other applications
-
4. End-User Verticals
- 4.1. Healthcare
- 4.2. Manufacturing
- 4.3. Utilities
- 4.4. BFSI
- 4.5. Retail
- 4.6. Government
- 4.7. Other end-user verticals
-
5. Geography
- 5.1. China
- 5.2. India
- 5.3. Japan
- 5.4. Other countries
APAC IoT Security Industry Segmentation By Geography
- 1. China
- 2. India
- 3. Japan
- 4. Other countries
APAC IoT Security Industry Regional Market Share
Geographic Coverage of APAC IoT Security Industry
APAC IoT Security Industry REPORT HIGHLIGHTS
| Aspects | Details |
|---|---|
| Study Period | 2020-2034 |
| Base Year | 2025 |
| Estimated Year | 2026 |
| Forecast Period | 2026-2034 |
| Historical Period | 2020-2025 |
| Growth Rate | CAGR of 19% from 2020-2034 |
| Segmentation |
|
Table of Contents
- 1. Introduction
- 1.1. Research Scope
- 1.2. Market Segmentation
- 1.3. Research Methodology
- 1.4. Definitions and Assumptions
- 2. Executive Summary
- 2.1. Introduction
- 3. Market Dynamics
- 3.1. Introduction
- 3.2. Market Drivers
- 3.2.1. Increasing Number of Data Breaches; Emergence of Smart Cities
- 3.3. Market Restrains
- 3.3.1 Growing Complexity among Devices
- 3.3.2 coupled with the Lack of Ubiquitous Legislation
- 3.4. Market Trends
- 3.4.1. Emergence of Smart City and Smart Home Developments to Drive the Market Growth
- 4. Market Factor Analysis
- 4.1. Porters Five Forces
- 4.2. Supply/Value Chain
- 4.3. PESTEL analysis
- 4.4. Market Entropy
- 4.5. Patent/Trademark Analysis
- 5. APAC IoT Security Industry Analysis, Insights and Forecast, 2020-2032
- 5.1. Market Analysis, Insights and Forecast - by Type of Security
- 5.1.1. Network Security
- 5.1.2. Endpoint Security
- 5.1.3. Application Security
- 5.1.4. Cloud Security
- 5.1.5. Other types of security
- 5.2. Market Analysis, Insights and Forecast - by Solutions
- 5.2.1. Identity Access Management (IAM)
- 5.2.2. Intrusion Prevention System (IPS)
- 5.2.3. Data Loss Protection (DLP)
- 5.2.4. Unified Threat Management (UTM)
- 5.2.5. Security & Vulnerability Management (SVM)
- 5.2.6. Network Security Forensics (NSF)
- 5.2.7. Other solutions
- 5.3. Market Analysis, Insights and Forecast - by Applications
- 5.3.1. Home Automation
- 5.3.2. Wearables
- 5.3.3. Manufacturing Process Management
- 5.3.4. Patient Information Management
- 5.3.5. Supply Chain Operation
- 5.3.6. Customer Information Security
- 5.3.7. Other applications
- 5.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 5.4.1. Healthcare
- 5.4.2. Manufacturing
- 5.4.3. Utilities
- 5.4.4. BFSI
- 5.4.5. Retail
- 5.4.6. Government
- 5.4.7. Other end-user verticals
- 5.5. Market Analysis, Insights and Forecast - by Geography
- 5.5.1. China
- 5.5.2. India
- 5.5.3. Japan
- 5.5.4. Other countries
- 5.6. Market Analysis, Insights and Forecast - by Region
- 5.6.1. China
- 5.6.2. India
- 5.6.3. Japan
- 5.6.4. Other countries
- 5.1. Market Analysis, Insights and Forecast - by Type of Security
- 6. China APAC IoT Security Industry Analysis, Insights and Forecast, 2020-2032
- 6.1. Market Analysis, Insights and Forecast - by Type of Security
- 6.1.1. Network Security
- 6.1.2. Endpoint Security
- 6.1.3. Application Security
- 6.1.4. Cloud Security
- 6.1.5. Other types of security
- 6.2. Market Analysis, Insights and Forecast - by Solutions
- 6.2.1. Identity Access Management (IAM)
- 6.2.2. Intrusion Prevention System (IPS)
- 6.2.3. Data Loss Protection (DLP)
- 6.2.4. Unified Threat Management (UTM)
- 6.2.5. Security & Vulnerability Management (SVM)
- 6.2.6. Network Security Forensics (NSF)
- 6.2.7. Other solutions
- 6.3. Market Analysis, Insights and Forecast - by Applications
- 6.3.1. Home Automation
- 6.3.2. Wearables
- 6.3.3. Manufacturing Process Management
- 6.3.4. Patient Information Management
- 6.3.5. Supply Chain Operation
- 6.3.6. Customer Information Security
- 6.3.7. Other applications
- 6.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 6.4.1. Healthcare
- 6.4.2. Manufacturing
- 6.4.3. Utilities
- 6.4.4. BFSI
- 6.4.5. Retail
- 6.4.6. Government
- 6.4.7. Other end-user verticals
- 6.5. Market Analysis, Insights and Forecast - by Geography
- 6.5.1. China
- 6.5.2. India
- 6.5.3. Japan
- 6.5.4. Other countries
- 6.1. Market Analysis, Insights and Forecast - by Type of Security
- 7. India APAC IoT Security Industry Analysis, Insights and Forecast, 2020-2032
- 7.1. Market Analysis, Insights and Forecast - by Type of Security
- 7.1.1. Network Security
- 7.1.2. Endpoint Security
- 7.1.3. Application Security
- 7.1.4. Cloud Security
- 7.1.5. Other types of security
- 7.2. Market Analysis, Insights and Forecast - by Solutions
- 7.2.1. Identity Access Management (IAM)
- 7.2.2. Intrusion Prevention System (IPS)
- 7.2.3. Data Loss Protection (DLP)
- 7.2.4. Unified Threat Management (UTM)
- 7.2.5. Security & Vulnerability Management (SVM)
- 7.2.6. Network Security Forensics (NSF)
- 7.2.7. Other solutions
- 7.3. Market Analysis, Insights and Forecast - by Applications
- 7.3.1. Home Automation
- 7.3.2. Wearables
- 7.3.3. Manufacturing Process Management
- 7.3.4. Patient Information Management
- 7.3.5. Supply Chain Operation
- 7.3.6. Customer Information Security
- 7.3.7. Other applications
- 7.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 7.4.1. Healthcare
- 7.4.2. Manufacturing
- 7.4.3. Utilities
- 7.4.4. BFSI
- 7.4.5. Retail
- 7.4.6. Government
- 7.4.7. Other end-user verticals
- 7.5. Market Analysis, Insights and Forecast - by Geography
- 7.5.1. China
- 7.5.2. India
- 7.5.3. Japan
- 7.5.4. Other countries
- 7.1. Market Analysis, Insights and Forecast - by Type of Security
- 8. Japan APAC IoT Security Industry Analysis, Insights and Forecast, 2020-2032
- 8.1. Market Analysis, Insights and Forecast - by Type of Security
- 8.1.1. Network Security
- 8.1.2. Endpoint Security
- 8.1.3. Application Security
- 8.1.4. Cloud Security
- 8.1.5. Other types of security
- 8.2. Market Analysis, Insights and Forecast - by Solutions
- 8.2.1. Identity Access Management (IAM)
- 8.2.2. Intrusion Prevention System (IPS)
- 8.2.3. Data Loss Protection (DLP)
- 8.2.4. Unified Threat Management (UTM)
- 8.2.5. Security & Vulnerability Management (SVM)
- 8.2.6. Network Security Forensics (NSF)
- 8.2.7. Other solutions
- 8.3. Market Analysis, Insights and Forecast - by Applications
- 8.3.1. Home Automation
- 8.3.2. Wearables
- 8.3.3. Manufacturing Process Management
- 8.3.4. Patient Information Management
- 8.3.5. Supply Chain Operation
- 8.3.6. Customer Information Security
- 8.3.7. Other applications
- 8.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 8.4.1. Healthcare
- 8.4.2. Manufacturing
- 8.4.3. Utilities
- 8.4.4. BFSI
- 8.4.5. Retail
- 8.4.6. Government
- 8.4.7. Other end-user verticals
- 8.5. Market Analysis, Insights and Forecast - by Geography
- 8.5.1. China
- 8.5.2. India
- 8.5.3. Japan
- 8.5.4. Other countries
- 8.1. Market Analysis, Insights and Forecast - by Type of Security
- 9. Other countries APAC IoT Security Industry Analysis, Insights and Forecast, 2020-2032
- 9.1. Market Analysis, Insights and Forecast - by Type of Security
- 9.1.1. Network Security
- 9.1.2. Endpoint Security
- 9.1.3. Application Security
- 9.1.4. Cloud Security
- 9.1.5. Other types of security
- 9.2. Market Analysis, Insights and Forecast - by Solutions
- 9.2.1. Identity Access Management (IAM)
- 9.2.2. Intrusion Prevention System (IPS)
- 9.2.3. Data Loss Protection (DLP)
- 9.2.4. Unified Threat Management (UTM)
- 9.2.5. Security & Vulnerability Management (SVM)
- 9.2.6. Network Security Forensics (NSF)
- 9.2.7. Other solutions
- 9.3. Market Analysis, Insights and Forecast - by Applications
- 9.3.1. Home Automation
- 9.3.2. Wearables
- 9.3.3. Manufacturing Process Management
- 9.3.4. Patient Information Management
- 9.3.5. Supply Chain Operation
- 9.3.6. Customer Information Security
- 9.3.7. Other applications
- 9.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 9.4.1. Healthcare
- 9.4.2. Manufacturing
- 9.4.3. Utilities
- 9.4.4. BFSI
- 9.4.5. Retail
- 9.4.6. Government
- 9.4.7. Other end-user verticals
- 9.5. Market Analysis, Insights and Forecast - by Geography
- 9.5.1. China
- 9.5.2. India
- 9.5.3. Japan
- 9.5.4. Other countries
- 9.1. Market Analysis, Insights and Forecast - by Type of Security
- 10. Competitive Analysis
- 10.1. Market Share Analysis 2025
- 10.2. Company Profiles
- 10.2.1 Wurldtech Security Technologies Inc
- 10.2.1.1. Overview
- 10.2.1.2. Products
- 10.2.1.3. SWOT Analysis
- 10.2.1.4. Recent Developments
- 10.2.1.5. Financials (Based on Availability)
- 10.2.2 FireEye Inc
- 10.2.2.1. Overview
- 10.2.2.2. Products
- 10.2.2.3. SWOT Analysis
- 10.2.2.4. Recent Developments
- 10.2.2.5. Financials (Based on Availability)
- 10.2.3 IBM Corporation
- 10.2.3.1. Overview
- 10.2.3.2. Products
- 10.2.3.3. SWOT Analysis
- 10.2.3.4. Recent Developments
- 10.2.3.5. Financials (Based on Availability)
- 10.2.4 Trend Micro Inc
- 10.2.4.1. Overview
- 10.2.4.2. Products
- 10.2.4.3. SWOT Analysis
- 10.2.4.4. Recent Developments
- 10.2.4.5. Financials (Based on Availability)
- 10.2.5 Infineon Technologies
- 10.2.5.1. Overview
- 10.2.5.2. Products
- 10.2.5.3. SWOT Analysis
- 10.2.5.4. Recent Developments
- 10.2.5.5. Financials (Based on Availability)
- 10.2.6 Gemalto NV*List Not Exhaustive
- 10.2.6.1. Overview
- 10.2.6.2. Products
- 10.2.6.3. SWOT Analysis
- 10.2.6.4. Recent Developments
- 10.2.6.5. Financials (Based on Availability)
- 10.2.7 Symantec Corporation (NortonLifeLock Inc)
- 10.2.7.1. Overview
- 10.2.7.2. Products
- 10.2.7.3. SWOT Analysis
- 10.2.7.4. Recent Developments
- 10.2.7.5. Financials (Based on Availability)
- 10.2.8 ARM Holdings PLC
- 10.2.8.1. Overview
- 10.2.8.2. Products
- 10.2.8.3. SWOT Analysis
- 10.2.8.4. Recent Developments
- 10.2.8.5. Financials (Based on Availability)
- 10.2.9 Sophos Group PLC
- 10.2.9.1. Overview
- 10.2.9.2. Products
- 10.2.9.3. SWOT Analysis
- 10.2.9.4. Recent Developments
- 10.2.9.5. Financials (Based on Availability)
- 10.2.10 Intel Corporation
- 10.2.10.1. Overview
- 10.2.10.2. Products
- 10.2.10.3. SWOT Analysis
- 10.2.10.4. Recent Developments
- 10.2.10.5. Financials (Based on Availability)
- 10.2.1 Wurldtech Security Technologies Inc
List of Figures
- Figure 1: APAC IoT Security Industry Revenue Breakdown (undefined, %) by Product 2025 & 2033
- Figure 2: APAC IoT Security Industry Share (%) by Company 2025
List of Tables
- Table 1: APAC IoT Security Industry Revenue undefined Forecast, by Type of Security 2020 & 2033
- Table 2: APAC IoT Security Industry Revenue undefined Forecast, by Solutions 2020 & 2033
- Table 3: APAC IoT Security Industry Revenue undefined Forecast, by Applications 2020 & 2033
- Table 4: APAC IoT Security Industry Revenue undefined Forecast, by End-User Verticals 2020 & 2033
- Table 5: APAC IoT Security Industry Revenue undefined Forecast, by Geography 2020 & 2033
- Table 6: APAC IoT Security Industry Revenue undefined Forecast, by Region 2020 & 2033
- Table 7: APAC IoT Security Industry Revenue undefined Forecast, by Type of Security 2020 & 2033
- Table 8: APAC IoT Security Industry Revenue undefined Forecast, by Solutions 2020 & 2033
- Table 9: APAC IoT Security Industry Revenue undefined Forecast, by Applications 2020 & 2033
- Table 10: APAC IoT Security Industry Revenue undefined Forecast, by End-User Verticals 2020 & 2033
- Table 11: APAC IoT Security Industry Revenue undefined Forecast, by Geography 2020 & 2033
- Table 12: APAC IoT Security Industry Revenue undefined Forecast, by Country 2020 & 2033
- Table 13: APAC IoT Security Industry Revenue undefined Forecast, by Type of Security 2020 & 2033
- Table 14: APAC IoT Security Industry Revenue undefined Forecast, by Solutions 2020 & 2033
- Table 15: APAC IoT Security Industry Revenue undefined Forecast, by Applications 2020 & 2033
- Table 16: APAC IoT Security Industry Revenue undefined Forecast, by End-User Verticals 2020 & 2033
- Table 17: APAC IoT Security Industry Revenue undefined Forecast, by Geography 2020 & 2033
- Table 18: APAC IoT Security Industry Revenue undefined Forecast, by Country 2020 & 2033
- Table 19: APAC IoT Security Industry Revenue undefined Forecast, by Type of Security 2020 & 2033
- Table 20: APAC IoT Security Industry Revenue undefined Forecast, by Solutions 2020 & 2033
- Table 21: APAC IoT Security Industry Revenue undefined Forecast, by Applications 2020 & 2033
- Table 22: APAC IoT Security Industry Revenue undefined Forecast, by End-User Verticals 2020 & 2033
- Table 23: APAC IoT Security Industry Revenue undefined Forecast, by Geography 2020 & 2033
- Table 24: APAC IoT Security Industry Revenue undefined Forecast, by Country 2020 & 2033
- Table 25: APAC IoT Security Industry Revenue undefined Forecast, by Type of Security 2020 & 2033
- Table 26: APAC IoT Security Industry Revenue undefined Forecast, by Solutions 2020 & 2033
- Table 27: APAC IoT Security Industry Revenue undefined Forecast, by Applications 2020 & 2033
- Table 28: APAC IoT Security Industry Revenue undefined Forecast, by End-User Verticals 2020 & 2033
- Table 29: APAC IoT Security Industry Revenue undefined Forecast, by Geography 2020 & 2033
- Table 30: APAC IoT Security Industry Revenue undefined Forecast, by Country 2020 & 2033
Frequently Asked Questions
1. What is the projected Compound Annual Growth Rate (CAGR) of the APAC IoT Security Industry?
The projected CAGR is approximately 19%.
2. Which companies are prominent players in the APAC IoT Security Industry?
Key companies in the market include Wurldtech Security Technologies Inc, FireEye Inc, IBM Corporation, Trend Micro Inc, Infineon Technologies, Gemalto NV*List Not Exhaustive, Symantec Corporation (NortonLifeLock Inc), ARM Holdings PLC, Sophos Group PLC, Intel Corporation.
3. What are the main segments of the APAC IoT Security Industry?
The market segments include Type of Security, Solutions, Applications, End-User Verticals, Geography.
4. Can you provide details about the market size?
The market size is estimated to be USD XXX N/A as of 2022.
5. What are some drivers contributing to market growth?
Increasing Number of Data Breaches; Emergence of Smart Cities.
6. What are the notable trends driving market growth?
Emergence of Smart City and Smart Home Developments to Drive the Market Growth.
7. Are there any restraints impacting market growth?
Growing Complexity among Devices. coupled with the Lack of Ubiquitous Legislation.
8. Can you provide examples of recent developments in the market?
August 2022 : Truvisor announced its partnership with One Identity, a unified identity security provider. The partnership would allow Truvisor to deliver One Identity solutions through their resellers' channels in Singapore, the Philippines, and Indonesia.
9. What pricing options are available for accessing the report?
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 4750, USD 4950, and USD 6800 respectively.
10. Is the market size provided in terms of value or volume?
The market size is provided in terms of value, measured in N/A.
11. Are there any specific market keywords associated with the report?
Yes, the market keyword associated with the report is "APAC IoT Security Industry," which aids in identifying and referencing the specific market segment covered.
12. How do I determine which pricing option suits my needs best?
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
13. Are there any additional resources or data provided in the APAC IoT Security Industry report?
While the report offers comprehensive insights, it's advisable to review the specific contents or supplementary materials provided to ascertain if additional resources or data are available.
14. How can I stay updated on further developments or reports in the APAC IoT Security Industry?
To stay informed about further developments, trends, and reports in the APAC IoT Security Industry, consider subscribing to industry newsletters, following relevant companies and organizations, or regularly checking reputable industry news sources and publications.
Methodology
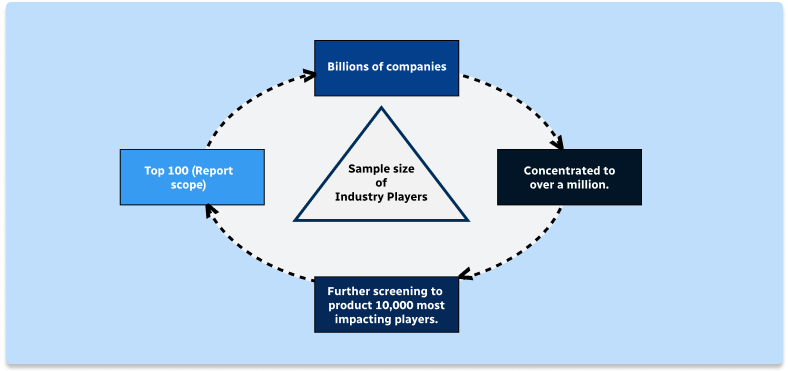
Step 1 - Identification of Relevant Samples Size from Population Database
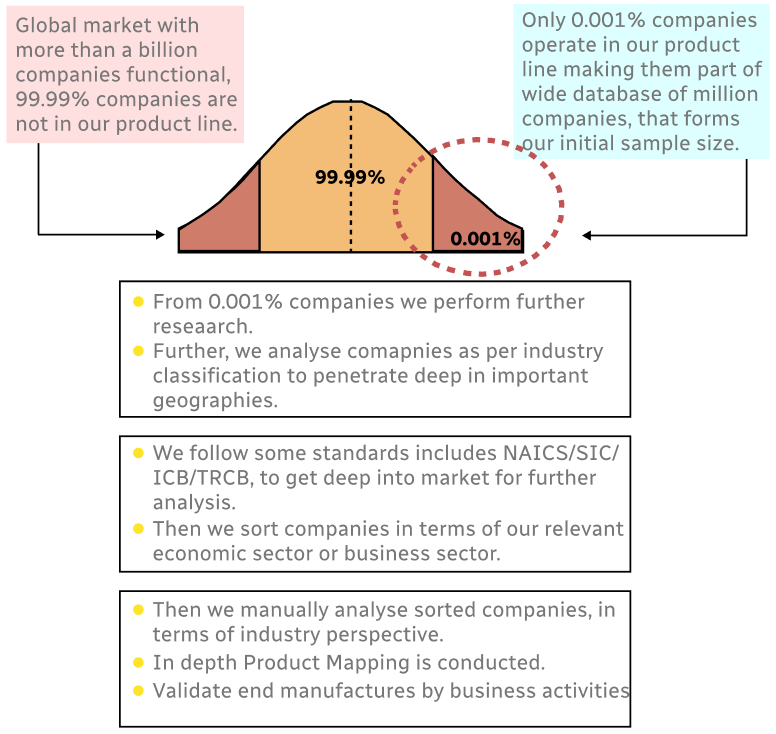
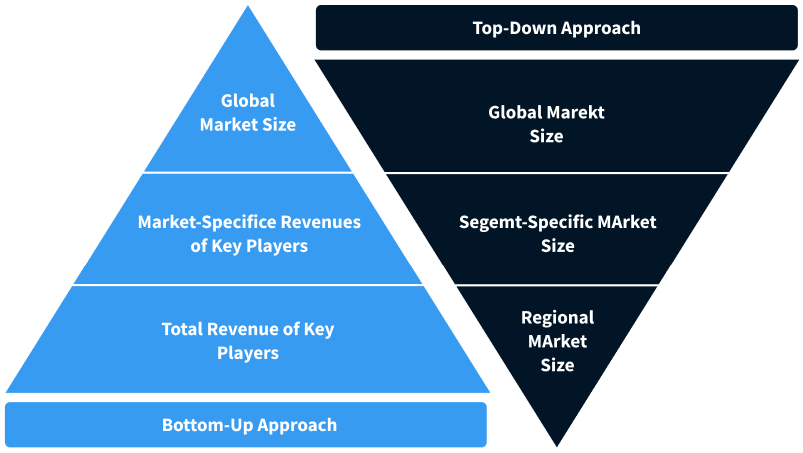
Step 2 - Approaches for Defining Global Market Size (Value, Volume* & Price*)
Note*: In applicable scenarios
Step 3 - Data Sources
Primary Research
- Web Analytics
- Survey Reports
- Research Institute
- Latest Research Reports
- Opinion Leaders
Secondary Research
- Annual Reports
- White Paper
- Latest Press Release
- Industry Association
- Paid Database
- Investor Presentations
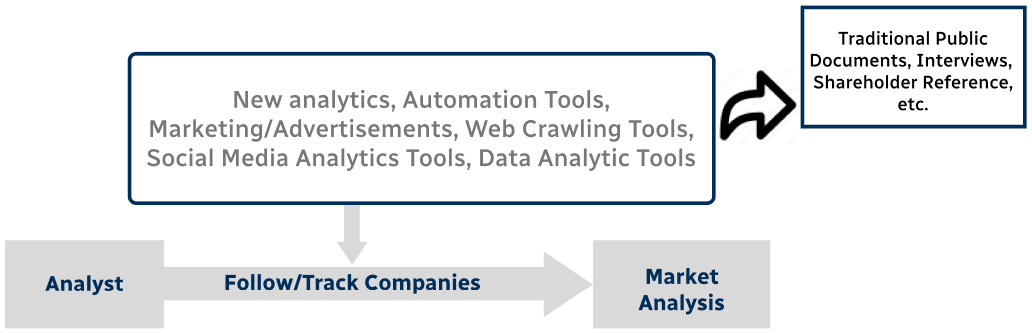
Step 4 - Data Triangulation
Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence


